SHA1:
- 27806e7f4a4a5e3236d52e432e982915ce636da4
A banking Trojan that targets Android devices. It is distributed under the guise of benign programs, e.g., Google programs with the Play Store icon.
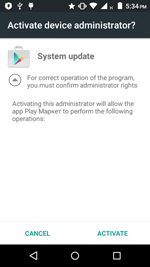
When launched, Android.BankBot.149.origin prompts the user to grant it administrative privileges and deletes its icon from the home screen.
The Trojan can receive the following commands from the command and control server:
- Send SMS – to send SMS;
- Go_P00t_request – to request administrator privileges;
- |UssDg0= - to send a USSD request;
- nymBePsG0 – to request the list of phone numbers from the contact list;
- |telbookgotext= – to send SMS messages with the text from its command to the entire contact list;
- Go_startPermis_request – to request additional permissions SEND_SMS, CALL_PHONE, READ_CONTACTS, ACCESS_FINE_LOCATION on devices with Android 6.0 and higher;
- Go_GPSlocat_request - to get GPS coordinates;
- state1letsgotxt - to receive an executable file containing a list of attacked banking applications;
- |startinj= – to display phishing window WebView with content downloaded from the link specified in a command.
Android.BankBot.149.origin checks a mobile device for the presence of the following banking applications and payment systems:
- Sberbank Online – ru.sberbankmobile;
- Sberbank Business Online – ru.sberbank_sbbol;
- Alfa-Bank - ru.alfabank.mobile.android;
- Alfa-Business – ru.alfabank.oavdo.amc;
- Visa QIWI Wallet - ru.mw;
- R-Connect mobile bank – ru.raiffeisennews;
- Tinkoff – com.idamob.tinkoff.android;
- PayPal – com.paypal.android.p2pmobile;
- WebMoney Keeper – com.webmoney.my;
- ROSBANK Online – ru.rosbank.android;
- VTB24-Online – ru.vtb24.mobilebanking.android;
- MTS Bank – ru.simpls.mbrd.ui;
- Yandex.Money: online payments – ru.yandex.money;
- Sberbank Onl@n PJSC SBERBANK - ua.com.cs.ifobs.mobile.android.sbrf;
- Privat24 – ua.privatbank.ap24;
- Russian Standard mobile bank – ru.simpls.brs2.mobbank;
- UBANK - financial supermarket - com.ubanksu;
- Idea Bank – com.alseda.ideabank;
- IKO – pl.pkobp.iko;
- Bank SMS – com.bank.sms;
- OTP Smart – ua.com.cs.ifobs.mobile.android.otp;
- VTB Online (Ukraine) – ua.vtb.client.android;
- Oschad 24/7 – ua.oschadbank.online;
- Platinum Bank – com.trinetix.platinum;
- UniCredit Mobile – hr.asseco.android.jimba.mUCI.ua;
- Raiffeisenbank Online – ua.pentegy.avalbank.production;
- Ukrgasbank – com.ukrgazbank.UGBCardM;
- StarMobile – com.coformatique.starmobile.android;
- Chase Mobile – com.chase.sig.android;
- Bank of America Mobile Banking – com.infonow.bofa;
- Wells Fargo Mobile – com.wf.wellsfargomobile;
- TD International – com.wsod.android.tddii;
- TD Spread Trading – com.directinvest.trader;
- Akbank Direkt – com.akbank.android.apps.akbank_direkt;
- Yapı Kredi Mobil Bankacılık – com.ykb.android;
- ÇEKSOR – com.softtech.iscek;
- JSC İŞBANK – com.yurtdisi.iscep;
- İşCep – com.pozitron.iscep;
- İşTablet – com.softtech.isbankasi.
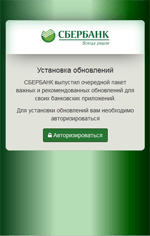
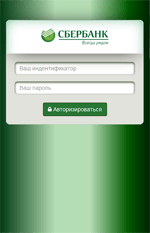
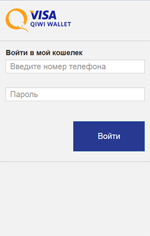
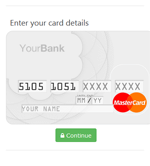
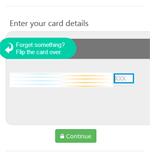
Information on found matches is sent to the C&C server. The Trojan receives a list of files to be monitored from execution. After one of them is launched, Android.BankBot.149.origin displays WebView on top of the attacked application with a fraudulent authentication form to access the user account. Then the entered information is sent to the server. The following are the examples of such fraudulent authentication forms:
Android.BankBot.149.origin also tries to steal bank card information. To do that, it tracks launch of the following programs:
- WhatsApp (com.whatsapp);
- Play Store – com.android.vending;
- Messenger – com.facebook.orca;
- Facebook – com.facebook.katana;
- WeChat – com.tencent.mm;
- Youtube – com.google.android.youtube;
- Uber – com.ubercab;
- Viber – com.viber.voip;
- Snapchat – com.snapchat.android;
- Instagram – com.instagram.android;
- imo – com.imo.android.imoim;
- Twitter – com.twitter.android.
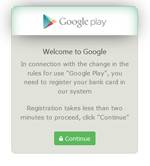
After the launch of one of these applications, the Trojan displays a bogus dialog resembling the one used to make purchases on Google Play:
When an SMS message arrives, the Trojan turns off all sounds and vibrations, sends the message content to the cybercriminals, and attempts to delete the original messages from the list of incoming SMS messages to hide them from the user.
Android.BankBot.149.origin also sends the server data on installed popular anti-virus software that can interfere with its work. To do that, the Trojan checks the device for the following applications:
- Anti-virus Dr.Web Light – com.drweb;
- CM Security AppLock AntiVirus – com.cleanmaster.security;
- Kaspersky Antivirus & Security – com.kms.free;
- ESET Mobile Security & Antivirus – com.eset.ems;
- Avast Mobile Security & Antivirus – com.avast.android.mobilesecurity;
- Clean Master (Boost&Antivirus) – com.cleanmaster.mguard;
- 360 Security - Antivirus – com.qihoo.security;
- AVG AntiVirus FREE for Android – com.antivirus;
- Antivirus Free - Virus Cleaner – com.zrgiu.antivirus;
- Super Cleaner - Antivirus – com.apps.go.clean.boost.master;
- AndroHelm AntiVirus Android 2017 – com.androhelm.antivirus.free;
- TrustGo Antivirus & Mobile Security – com.trustgo.mobile.security;
- Sophos Free Antivirus and Security – com.sophos.smse.