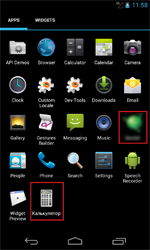
A malicious program for Android mobile devices. It may be distributed under the guise of various applications. This bot can perform multiple actions upon receiving a command from cybercriminals. The main aim of this Trojan is stealing money from bank accounts of Russian users.
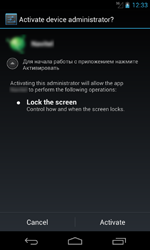
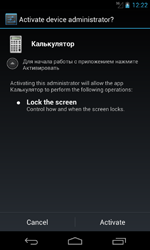
When launched, Android.BankBot.33.origin tries to gain access to administrator privileges of the mobile device showing the appropriate system prompt until the victim gives consent. Then, depending on modification, the malware displays a message about the allegedly occurred error or displays the application interface that the Trojan used to get onto the mobile device. After this, the bot deletes its shortcut from the home screen.
 |
 |
 |
 |
Then the Trojan connects to the command and control server (C&C server) located at http://xxxx.xx.214.97/task.php and loads the following information about the infected device:
- IMEI
- IMSI
- Сurrent system time
- Mobile number
- Trojan version
- SID
- OS version
- Device model
- Device manufacturer
- SDK system version
- Trojan's identifier
In return the bot receives a list of the following commands transferred to it in JSON format:
- 8e9ql9skqf—establish the time of the next connection to the command center
- server—change the address of the command center
- izqfugi7n8—record the list of numbers in the configuration file, so that all messages from those numbers are concealed from the user
- mzybm1q2eh—record the list of numbers in the configuration file, so that all messages from those numbers are transmitted to the C&C server
- hgany9c0rj—clean the configuration file from the contacts whose messages are hidden
- tyo2pxb1wr—clean the configuration file from the contacts whose messages are transmitted to the C&C server
- gz7j2ph7eg—send SMS with a predefined text to a number specified in the command
- ligtd7jxxr—download and try to install the application (must be confirmed by the user)
- hmq3nlddk3—try to remove the application specified in the command (must be confirmed by the user)
- notification—display a message in the notification area with the text specified in the command
- 1lo8lsn7un—open the web address specified in the command
- ozs44xicjk—send the contact list to the C&C server
- 88h4s39ead—send the list of installed applications to the C&C server
The Trojan sends SMS to the customer service numbers of several Russian banks as well as to one of the most popular payment services in order to obtain information about the user's bank account and bank cards. When the necessary information is obtained, Android.BankBot.33.origin transfers all available funds by means of special SMS commands to the cybercriminals' account.