SHA1: 9a8f33c8f7ef02d2551331023bc90f8990645d5d
c56da810fc0bd6ce61313afdba492942715c2720
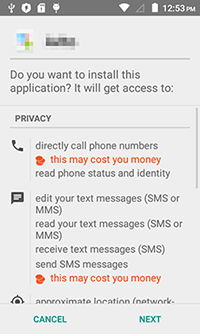
A Trojan targeting Android devices. It can be distributed via SMS spam containing links to allegedly harmless programs, for example, a client application for a well-known advertising website, software to view MMS messages, and so on. The Trojan is implemented as a bot that can execute commands issued by cybercriminals and steal money from bank accounts of Android users.
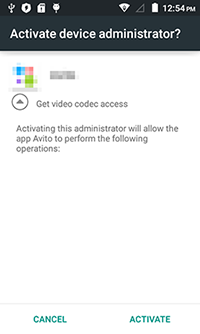
Once the malicious program acquires necessary privileges, it removes the shortcut from the Home Screen.
Some modifications of this Trojan do not ask the user for administrator privileges—they just activate the malicious system process and, after that, remove the shortcut.
Using a POST request, Android.SmsBot.459.origin sends the following information to the command and control server:
- IMEI
- Model name
- Current system language
- IMSI
- Mobile number
- Mobile network operator name
- OS version
- Data on availability of Viber
- Trojan’s version
- Unique Trojan's ID generated for the infected device
As a reply, the Trojan receives a command to check the device for online banking applications of several financial organizations, such as Alfa-Bank and Sberbank of Russia. The malware also checks balances of relevant bank accounts, QIWI wallet, and the user's mobile account.
The Trojan can execute the following commands:
- esms&&&—send a list of all SMS messages to the server,
- getapps&&&—send a list of installed applications to the server,
- sent&&&—send an SMS with a predefined text to the specified number,
- rent&&&—enable intercepting SMS messages,
- sms_stop&&&—disable intercepting SMS messages,
- ussd&&&—send a USSD query,
- export&&&—send a list of contacts to the server,
- u&&&—set a new command and control server address,
- sapp&&&—send a message to the specified number via Viber.
The Trojan sends execution reports to the command and control server via POST requests as follows:
{"command":"sent&&&","timestamp":"934629","id":"5f2b6fec-2e27-4a72-90f7-6fea6d6d1a81",
"type":"result","status":"ok"}The malware conceals all intercepted SMS messages from the user forwarding them in POST requests to the command and control server as follows:
{"data":"2015:09:18_14:05:20","id":"5f2b6fec-2e27-4a72-90f7-6fea6d6d1a81",
"text":"Балансы: 0 руб.","number":"QIWI WALLET","type":"load"}To hide incoming messages from the owner of the device,Android.SmsBot.459.origin uses the following function:
this.abortBroadcast();Then it disables all sound alerts (including vibro call) as follows:
this.getSystemService("audio").setRingerMode(0);Next, the Trojan deletes an incoming text from the memory:
this.a.getContentResolver().delete(Uri.parse(String.valueOf(v9) + v6_1), null, null);After 3 seconds, sound alerts are enabled again:
v0 = 3000;
Thread.sleep(v0);
this.a.getSystemService("audio").setRingerMode(2);