SHA1: 89dee7086968dda688703304fd4b5163476b7f44
A Trojan for Android that steals confidential information and delivers advertisements. It is distributed via bogus versions of popular Android applications on the Google Play store.
Once launched, it sends the following information to the command and control server:
- “email”—email address connected to a Google user account. It is obtained from AccountManager; at that, only getAccountsByType("com.google”) is used;
- “app_id”—meta-data from the manifest.xml file of the infected application;
- “gcm_id”—GCM identifier (Google Cloud Messaging id);
- “sender_id”—the application identifier specified by the server;
- “app_version_code”—android:versionCode from the manifest.xml file;
- “package_name”—name of the package containing the Trojan;
- “sdk_version_name”—SDK version;
- “sdk_version_code”—the Trojan’s SDK build number;
- “android_id”—unique identifier;
- “imei”—IMEI identifier;
- “android_version”—operating system version;
- “model”—mobile device model;
- “screen”—screen resolution;
- “phone”—cell phone number;
- “api_version”—SDK version of the application;
- “country”—the user’s geolocation;
- “cpu”—CPU type;
- “mac”—MAC address of the power adapter;
- “user_agent”—generates User Agent line for a certain device, considering such parameters as Build.VERSION.RELEASE, Build.VERSION.CODENAME, and Build.MODEL, Build.ID;
- “carrier”—mobile network operator;
- “is_plugin”—informs the server whether the Trojan is launched from the original aaplication (the false value) or from its plug-in located in its software resources (the false value);
- “time_from_begin”—specifies a time period after which the Trojan starts transmitting data to the server;
- “install_referrer”—by default, sends the "Others” value;
- “connection_type”—network connection type;
- “connection_sub_type”—network subtype;
- “is_rooted”—availability of root access (the true or false value);
- “active_device_admin”—indicates whether an infected application has administrator privileges (the true or false value);
- “has_gp”—indicates whether a Google Play application is on the device (the true or false value);
- "Install from = " - "Google Play”/”Others”—indicates whether the infected application is installed from Google Play or from a third-party app store.
Once any of installed applications is launched, the Trojan sends a POST request that contains the above-mentioned information, adding the name of the running application’s package and requesting advertising parameters:
- "index" – requestads;
- “package_name_running”—name of the running application.
Depending on a received command, Android.Spy.277.origin can execute the following actions:
- “show_log”—enable or disable logging;
- “install_plugin”—install a plug-in hidden inside the malicious application;
- “banner”, “interstitial”, “video_ads”—display different types of advertisements (including, on top of the OS interface and other applications);
- “notification”—display a notification with the received parameters;
- “list_shortcut”—create shortcuts on the home screen (tapping these shortcuts leads to opening of specified sections in Google Play);
- “redirect_gp”—open a webpage with a specified address in Google Play;
- “redirect_browse”—open a specified webpage in a preinstalled browser;
- “redirect_chrome”—open a specified webpage in Chrome;
- “redirect_fb”—open a Facebook webpage specified by the command.
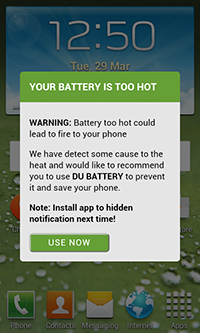
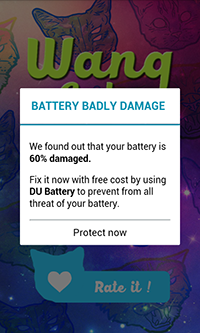
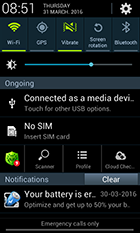
Examples of advertising images:
Examples of advertisements in the status bar:
Examples of shortcuts created by the Trojan:
At present, more than 100 applications are known to contain Android.Spy.277.origin:
- com.true.icaller
- com.appstorenew.topappvn
- com.easyandroid.free.ios6
- com.entertainmentphotoedior.photoeffect
- lockscreenios8.loveslockios.com.myapplication
- com.livewallpaper.christmaswallpaper
- com.entertainment.drumsetpro
- com.entertainment.nocrop.nocropvideo
- com.entertainment.fastandslowmotionvideotool
- com.sticker.wangcats
- com.chuthuphap.xinchu2016
- smartapps.cameraselfie.camerachristmas
- com.ultils.scanwifi
- com.entertainmenttrinhduyet.coccocnhanhnhat
- com.entertainment.malmath.apps.mm
- com.newyear2016.framestickertet
- com.entertainment.audio.crossdjfree
- com.igallery.styleiphone
- com.crazystudio.mms7.imessager
- smartapps.music.nhactet
- com.styleios.phonebookios9
- com.battery.repairbattery
- com.golauncher.ip
- com.photo.entertainment.blurphotoeffect.photoeffect
- com.irec.recoder
- com.Jewel.pro2016
- com.tones.ip.ring
- com.entertainment.phone.speedbooster
- com.noelphoto.stickerchristmas2016
- smartapps.smstet.tinnhantet2016
- com.styleios9.lockscreenchristmas2016
- com.stickerphoto.catwangs
- com.ultils.frontcamera
- com.phaotet.phaono2
- com.video.videoplayer
- com.entertainment.mypianophone.pianomagic
- com.entertainment.vhscamcorder
- com.o2yc.xmas
- smartapps.musictet.nhacxuan
- com.inote.iphones6
- christmas.dhbkhn.smartapps.christmas
- com.bobby.carrothd
- om.entertainment.camera.fisheyepro
- com.entertainment.simplemind
- com.icall.phonebook.io
- com.entertainment.photo.photoeditoreffect
- com.editphoto.makecdcover
- com.tv.ontivivideo
- smartapps.giaixam.gieoquedaunam
- com.ultils.frontcamera
- com.applock.lockscreenos9v4
- com.beauty.camera.os
- com.igallery.iphotos
- com.calculator.dailycalories
- com.os7.launcher.theme
- com.trong.duoihinhbatchu.chucmungnammoi
- com.apppro.phonebookios9
- com.icamera.phone6s.os
- com.entertainment.video.reversevideo
- com.entertainment.photoeditor.photoeffect
- com.appvv.meme
- com.newyear.haitetnew
- com.classic.redballhd
- com.entertainmentmusic.musicplayer.styleiphoneios
- com.camera.ios8.style
- com.countdown.countdownnewyear2016
- com.photographic.iphonecamera
- com.contactstyle.phonebookstyleofios9
- com.entertainment.blurphotobackground.photoeffect.cameraeditor.photoeffect
- com.color.christmas.xmas
- com.bottle.picinpiccamera
- com.entertainment.videocollagemaker
- com.wallpaper.wallpaperxmasandnewyear2016
- com.ultils.lockapp.smslock
- com.apppro.phonebookios9
- com.entertainment.myguitar.guitarpro
- com.sticker.stickerframetet2016
- com.bd.android.kmlauncher
- com.entertainment.batterysaver.batterydoctor
- com.trong.jumpy.gamehaynhatquadat
- com.entertainmentphotocollageeditor
- smartapps.smsgiangsinh.christmas2016
- smartapps.musicchristmas.christmasmusichot
- com.golauncher.ip
- com.applock.lockscreenos9v4
- com.imessenger.ios
- com.livewall.paper.xmas
- com.main.windows.wlauncher.os.wp
- com.entertainmentlaunchpad.launchpadultimate
- com.fsoft.matchespuzzle
- com.entertainment.photodat.image.imageblur
- com.videoeditor.instashot
- com.entertainment.hi.controls
- com.icontrol.style.os
- smartapps.zing.video.hot
- com.photo.entertainment.photoblur.forinstasquare
- com.entertainment.livewallpaperchristmas
- com.entertainment.tivionline
- com.iphoto.os
- com.tool.batterychecker
- com.photo.multiphotoblur
- smartapps.nhactet.nhacdjtet
- com.runliketroll.troll
- com.jinx.metalslug.contra