SHA1:
b607191448d0c31ea7d4a4ce9a0268cc72a23701
c80ce28bae65d06c6855b0e2647f752a3b7c4fbe
18747eaf81daaf51abe76749dc6fa89937e2a6f5
A Trojan for Android designed to steal user login credentials needed to access online banking programs and to steal money from victims’ bank accounts. Android.SmsSpy.88.origin is distributed under the guise of benign applications—for example, Adobe Flash Player.
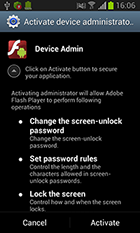
When launched, the Trojan prompts the user to grant it administrative privileges:
The Trojan is distributed under the guise of a benign application, for example, Adobe Flash Player. Once launched, the Trojan prompts the user to grant it administrator privileges. It then turns on the Wi-Fi module and checks every second whether a Wi-Fi or cellular connection has been established. If no connection is made, Android.SmsSpy.88.origin enables these communication channels once again.
Then the Trojan sends the following information to the command and control server:
- Infected device's unique identifier generated by the Trojan
- IMEI identifier
- Current system language
- Mobile network operator
- OS version
- Mobile device model
- Cell phone number
Stealing authentication information
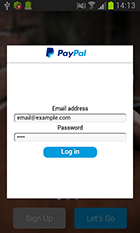
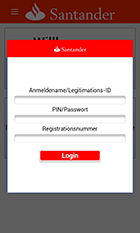
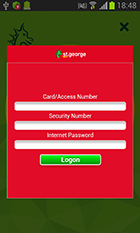
The configuration file of Android.SmsSpy.88.origin contains a list of online banking applications and links to phishing dialog templates for these applications. For example:
- "com.paypal.android.p2pmobile" – "http://******merti.com/333/l/pl/paypal.php"
- "de.commerzbanking.mobil" – "http://******merti.com/333/l/de/06.php"
- "com.ing.diba.mbbr2" – "http://******merti.com/333/l/de/13.php"
- "de.ing_diba.kontostand" – "http://******merti.com/333/l/de/13.php"
- "de.fiducia.smartphone.android.banking.vr" – "http://******merti.com/333/l/de/15.php"
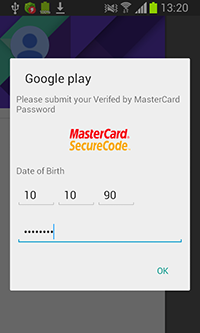
Android.SmsSpy.88.origin keeps track of when any of the above-listed applications are launched. If a launch is detected, the Trojan downloads a phishing input form from the server and displays it on top of the running application. All information entered by the user is then sent to cybercriminals. Phishing dialogs may look as follows:
Stealing credit card information
Android.SmsSpy.88.origin also attempts to steal user bank card information by tracking the launch of the following applications specified in its configuration (this list can different application names depending on the Trojan’s modification):
- com.android.vending;
- com.viber.voip;
- com.whatsapp;
- com.skype.raider;
- com.facebook.orca;
- com.facebook.katana;
- com.instagram.android;
- com.android.chrome;
- com.twitter.android;
- com.google.android.gm;
- com.android.calendar;
- jp.naver.line.android.
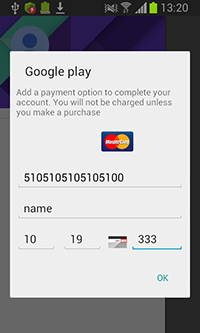
Once the Trojan detects that one of the above-mentioned applications is running, it displays a bogus dialog resembling the one used to make purchases on Google Play, prompting the user to enter their bank card information:
All the entered information is then transmitted to the server.
Command executing
Android.SmsSpy.88.origin can receive the following commands from the server:
- rent&&&—start intercepting all incoming SMS messages;
- sms_stop&&&—stop intercepting incoming SMS messages;
- sent&&&—send a text message;
- ussd&&&—send the USSD request;
- delivery&&&—send SMS messages to all contact list numbers;
- apiserver—change the address of the command and control server;
- appmass—send an MMS message;
- windowStop—add a specified application to the exclusion list so that when that application is launched, a phishing dialog is not displayed;
- windowStart—delete a specified application from the exclusion lists;
- windowsnew—download an updated executable file containing a list of attacked applications from the server;
- UpdateInfo—send information about all installed applications to the server;
- freedialog—display a template-based dialog using WebView (this command is applied to activate the screen lock function)
- freedialogdisable—cancel the display of the WebView dialog;
- adminPhone—change the phone number used to send SMS messages that repeat commands;
- killStart—set the password for ScreenLock;
- killStop—clear the password from ScreenLock;
- upload_sms—send all saved SMS messages to the server;
- notification—display a notification with the received parameters.
The Trojan can also receive the rent&&&, sent&&&, ussd&&&, killStart, and killStop commands as text messages from cybercriminals.
If a command is executed successfully, the malicious program reports this information to the server by sending the POST request:
POST HTTP/1.1 http://******merti.com/333/set_result.php
Content-Length: 61
Content-Type: application/x-www-form-urlencoded
Host: ******merti.com
Connection: Keep-Alive
bot_id=**********260a5fc56212793aca5387&result=windowStart+OK
Resistance to anti-virus software
Android.SmsSpy.88.origin tries to hinder the work of some anti-virus programs and service utilities, preventing them from launching. Depending on the Trojan modification involved, these programs can include:
- com.cleanmaster.security;
- com.cleanmaster.mguard;
- com.piriform.ccleaner;
- com.cleanmaster.mguard_x86;
- com.cleanmaster.sdk;
- com.cleanmaster.boost;
- com.drweb;
- com.qihoo.security;
- com.kms.free;
- com.eset.ems2.gp;
- com.qihoo.security.lite;
- com.symantec.mobilesecurity;
- com.dianxinos.optimizer.duplay.
Names of banking applications attacked
The following online banking applications are currently known to be attacked by the Trojan:
- at.bawag.mbanking
- at.easybank.mbanking
- at.spardat.netbanking
- at.volksbank.volksbankmobile
- au.com.bankwest.mobile
- au.com.ingdirect.android
- au.com.nab.mobile
- Citibank.CZ
- com.akbank.android.apps.akbank_direkt
- com.arkea.android.application.cmb
- com.arkea.android.application.cmso2
- com.bankaustria.android.olb
- com.bbva.bbvacontigo
- com.bbva.bbvawallet
- com.bbva.nxt_tablet
- com.boursorama.android.clients
- com.cacf.MonCACF
- com.caisseepargne.android.mobilebanking
- com.cajamar.Cajamar
- com.chase.sig.android
- com.cic_prod.bad
- com.citi.citimobile
- com.citiuat
- com.cm_prod.bad
- com.comarch.mobile
- com.commbank.netbank
- com.CreditAgricole
- com.db.mm.deutschebank
- com.discoverfinancial.mobile
- com.finansbank.mobile.cepsube
- com.fullsix.android.labanquepostale.accountaccess
- com.garanti.cepsubesi
- com.getingroup.mobilebanking
- com.getingroup.mobilebanking
- com.groupama.toujoursla
- com.grppl.android.shell.CMBlloydsTSB73
- com.grppl.android.shell.halifax
- com.idamob.tinkoff.android
- com.infonow.bofa
- com.ing.diba.mbbr2
- com.IngDirectAndroid
- com.isis_papyrus.raiffeisen_pay_eyewdg
- com.konylabs.CBHU
- com.konylabs.cbplpat
- com.lbp.peps
- com.macif.mobile.application.android
- com.ocito.cdn.activity.creditdunord
- com.paypal.android.p2pmobile
- com.pozitron.iscep
- com.regions.mobbanking
- com.starfinanz.mobile.android.dkbpushtan
- com.starfinanz.smob.android.sbanking
- com.starfinanz.smob.android.sfinanzstatus
- com.tmobtech.halkbank
- com.usaa.mobile.android.usaa
- com.vakifbank.mobile
- com.ykb.android
- com.ziraat.ziraatmobil
- de.adesso.mobile.android.ga
- de.adesso.mobile.android.gad
- de.comdirect.android
- de.commerzbanking.mobil
- de.consorsbank
- de.dkb.portalapp
- de.fiducia.smartphone.android.banking.vr
- de.ing_diba.kontostand
- de.postbank.finanzassistent
- es.bancopopular.android.lanzadera
- es.bancosantander.apps
- es.lacaixa.mobile.android.newwapicon
- eu.eleader.mobilebanking.pekao
- eu.eleader.mobilebanking.raiffeisen
- fr.axa.monaxa
- fr.banquepopulaire.cyberplus
- fr.banquepopulaire.cyberplus.pro
- fr.creditagricole.androidapp
- fr.lcl.android.customerarea
- fr.lemonway.groupama
- mobi.societegenerale.mobile.lappli
- mobile.santander.de
- net.bnpparibas.mescomptes
- net.inverline.bancosabadell.officelocator.android
- org.banksa.bank
- org.stgeorge.bank
- org.westpac.bank
- pl.bzwbk.bzwbk24
- pl.bzwbk.mobile.tab.bzwbk24
- pl.eurobank
- pl.ing.ingmobile
- pl.mbank
- pl.pkobp.iko
- ru.alfabank.mobile.android
- ru.mw
- ru.sberbankmobile
- ru.vtb24.mobilebanking.android
- uk.co.tsb.mobilebank
- wit.android.bcpBankingApp.millenniumPL